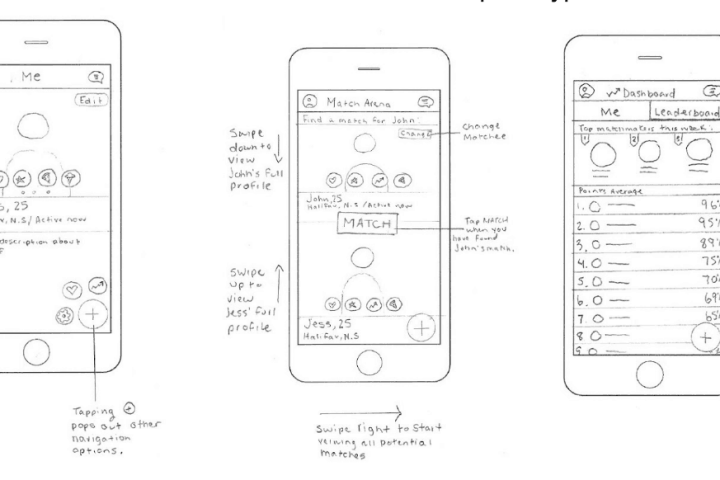
Recently, I had the opportunity to review a project that had gone off the rails. The parties were the inventors (non-technical, co-founders) and the developer (a contracted entity.) The contract between the entities clearly laid out a set of deliverables that the developer would create based upon a somewhat flexible...Continue reading
Category: Expert
Time is of the Essence
If you find yourself the victim of electronic theft, you should not drag your feet in taking action. Why? Because vital evidence you may need in the future vanishes as time progresses. Many different kinds of information are recorded in log files when activities occur using your devices, accounts, and...Continue reading
Phone Hacked, Part 2
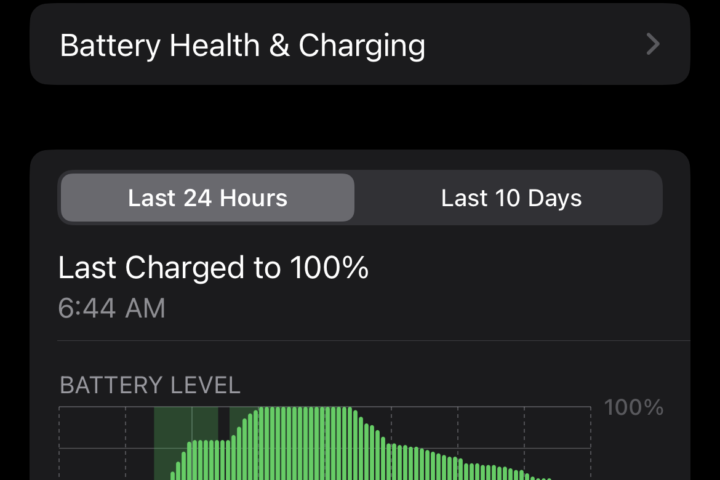
In part 1 of this series, there were a number of common sense steps suggested to secure your phone to prevent unauthorized access. In this entry, we will provide some pointers as to how you can determine if your phone has been compromised. Often, the battery is the best indicator...Continue reading
Phone hacked?
One of the most common questions I am asked by clients is “How can I determine if my phone has been hacked?” When a person reaches this point, typically it is the result of odd behavior of the device in question and/or unexplained information leakage. It’s unsettling and concerning when...Continue reading