In part 1 of this series, there were a number of common sense steps suggested to secure your phone to prevent unauthorized access. In this entry, we will provide some pointers as to how you can determine if your phone has been compromised.
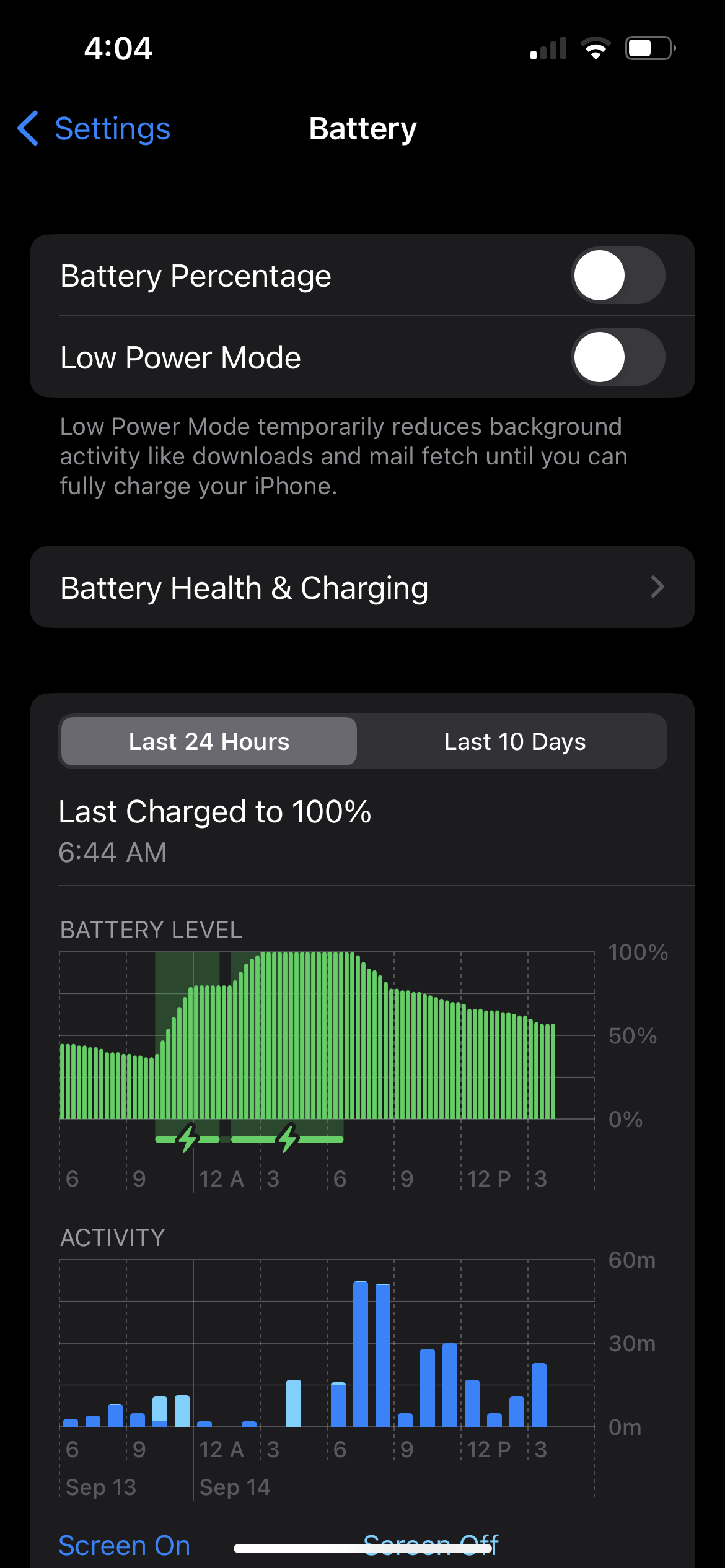
Often, the battery is the best indicator that there is something amiss in your device. If you are noticing that the battery is draining more quickly than usual and your habits and applications haven’t changed, this can be a sign that a rogue piece of software has taken up residence inside your device. In nearly all smart phones in the settings, there is information about battery usage, battery life, and how the battery is being consumed. On an Apple device for instance, one would select Settings, pull down to get a search settings entry, then type battery.
The resulting screen shows battery display options and a chart of usage that can be either the past 24 hours (default) or past 10 days. We recommend the 10 day view as the most useful. Scrolling further down will show a list of applications and their relative energy consumption as a percentage. Look at these items closely, does it match your typical phone usage? For instance, one might be a gamer or social media participant, are the expected applications listed toward the top of the list? Do you not recognize any of the apps?
This information can provide you a clue about what might be happening on your phone. As previously discussed, turn off location services and permission for applications to run in the background. What you might believe is bad activity could simply be a poorly designed application running in the background disproportionately consuming resources. Check in on the battery information again in a day or so to see what has changed.
But what if there is a power hungry app I don’t recognize? You should take steps to remove that application, back up your phone. Perform a factory reset, and then restore from backup. Using a malware scanner / detector (many are available on app stores for pay or free usage) check to see if there are any hits. If not, back your phone up again at this point as a good image and continue to monitor usage. It is also a good idea to change passwords for applications and websites that the phone has had access to.
Other signs your phone might be compromised include images that you do not recognize in your photos folder, weird text messages that appear to have originated from you that you did not send, strange phone numbers in your outgoing call list, and so on. Weird and unexplained behavior that you do not recognize. We recommend keeping control of your device at all times, protecting it with a non-trivial passcode, thinking carefully about enabling/using biometrics, and sharing your device with no one.
If you find that you have this situation and these steps are outside your comfort zone, contact us. We can help evaluate the state of your device and either recommend how to recover it or do it for you.